Operational Technology / Industrial Control Systems (OT/ICS)
More and more companies are integrating production facilities into their existing IT systems in order to operate more efficiently. However, this makes the systems increasingly vulnerable to attackers. We show you how to protect OT environments.

- Home
- Operational Technology
OT risk analysis with Controlware
What can we do for you?
Given the attractive potential for efficiency and automation, many companies are pushing ahead with the convergence of their IT and OT environments. However, they often find it difficult to evaluate the risks that arise for their OT environment. And that is understandable – after all, every OT system is unique. Accordingly, risk assessment and protection must also be tailor-made. Controlware experts support you in analyzing and minimizing your risks.
Our starting point is a comprehensive risk analysis, which, as an ongoing process, requires a thorough knowledge of the specific OT/IT infrastructure and culture of the company.
ISO 31000, the ISO standard for risk management, defines risk as follows:
Risk = damage x probability of occurrence
Based on the risk analysis, we then work with your team to assess the maturity level of your OT security, develop a customized action plan, and set the course for proactive risk management.
Solution descriptions
Your benefits with Controlware
Years of experience in IT and OT infrastructures
Reliable detection and categorization of risks
Identification of critical assets and components
Development and implementation of a long-term security strategy
Implementation of a zone concept
Support with the integration of our partners' solutions
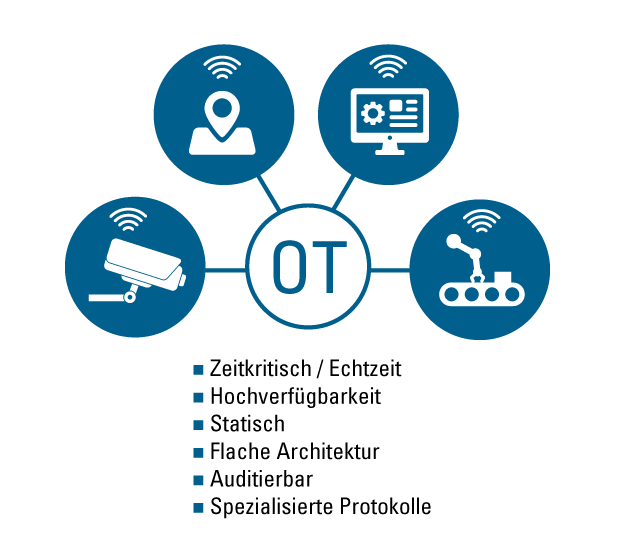
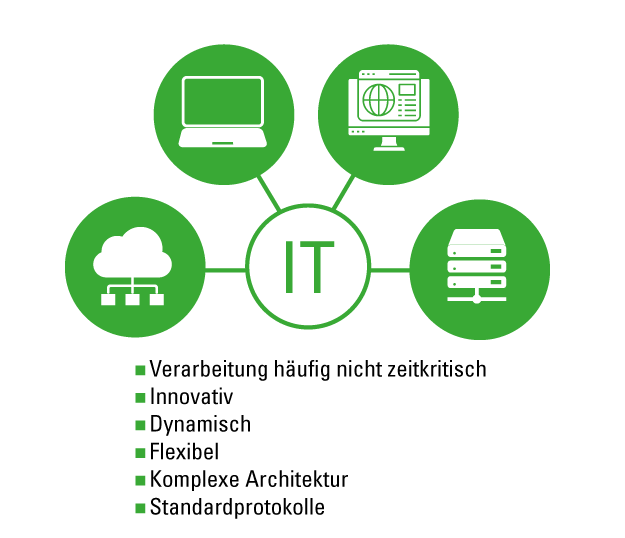
What distinguishes information technology (IT) from operational technology (OT)

IT and OT are converging—and can undoubtedly benefit from each other. However, to exploit this potential, you first need to understand the differences between IT and OT:
OT, or operational technology, controls physical devices, while IT deals with the management and protection of data. OT therefore focuses on physical processes, such as the control and availability of operational technology. IT, on the other hand, focuses on ensuring the confidentiality, integrity, and availability of systems and information.
These differences require customized security strategies to securely connect IT and OT. An OT zone concept and a well-thought-out OT architecture design create clear security boundaries, increase resilience, and enable efficient integration of both worlds.
Solution decriptions
How you can benefit from converging your IT and OT environments
The seamless integration of IT and OT environments makes your company more agile, opens up new automation potential, and helps you make informed decisions based on robust data.
- Improved efficiency
-
When IT and OT environments converge, you can collect, analyze, and utilize data in real time to make better decisions and optimize processes—for example, to set the course for predictive maintenance procedures.
- Faster decision-making
-
Easy access to IT and OT data enables you to respond quickly to changes in production or demand, opening up attractive growth opportunities.
- Greater security
-
By integrating OT systems into your security architecture, you can better coordinate security measures for IT and OT. This minimizes threats in both the digital and physical worlds.
- Innovation and flexibility
-
The convergence of networks simplifies the introduction of innovative technology solutions such as IoT (Internet of Things), edge computing, and artificial intelligence in industrial environments.
- Complete compliance
-
The consolidation of all IT and OT data helps you comply with regulatory requirements – from the EU's NIS 2 Directive to a wide range of industry standards.
What you need to consider when integrating IT and OT
The convergence of IT and OT infrastructures also poses risks. We help you reap the benefits without compromising security and compliance.
- New security risks
-
The integration of IT and OT systems is often problematic from a security perspective, as OT systems are generally protected differently than IT systems: While the focus in OT systems is on system security, data security is the primary concern in IT. Furthermore, IT security is usually based on the principle of “best effort,” while OT follows a “worst-case” approach.
- Unclear priorities
-
IT and OT traditionally have different priorities: IT focuses on data integrity, information security, and network protection, while OT places greater emphasis on physical processes and industrial control systems and their operability. Make sure you take both requirements into account—and ensure open, cross-departmental communication!
- Cultural differences
-
The cultural differences between OT and IT are the result of different working approaches, goals, and historical developments that influence how employees work, communicate, and set priorities.
- Complexity of integration
-
The technical integration of IT and OT systems is complex and time-consuming, especially when older industrial plants with many legacy systems need to be connected. In such cases, it has proven beneficial to bring in external partners at an early stage, who can achieve the desired results more quickly thanks to their many years of experience.
Possible consequences of damage
- Loss of sensitive data
- Manipulation of data
- Production downtime
- Service interruptions
- Personal injury
- Environmental damage
- Financial damage (direct and indirect)
- Compliance violations and resulting heavy penalties
- Liability risks
Potential threats
- Introduction of malware via removable media and mobile systems
- Infection with malware via the Internet and intranet
- Human error or sabotage
- Compromise of extranet and cloud components
- Social engineering and phishing
- DDoS attacks
- Control components connected to the Internet
- Intrusion via remote maintenance access
- Technical error and force majeure
- Software and hardware vulnerabilities in the supply chain
OT-Security Operations Center
An OT Security Operations Center (OT-SOC) monitors and protects your operational technology around the clock. It detects threats in real time, responds quickly to security incidents, and minimizes risks to your critical systems. With customized solutions such as anomaly detection and SIEM systems, an OT-SOC ensures that your OT infrastructure is protected against cyberattacks and that operational processes run securely and reliably at all times.
Solution Descriptions
Contact
Do you have any questions? Our Operational Technology team will be happy to assist you.